Understanding Yara, Sigma, and Snort Rules in Cybersecurity
Understanding Yara, Sigma, and Snort Rules in Cybersecurity
In the field of cybersecurity, Yara , Sigma , and Snort are essential tools used for creating and implementing rules to detect and respond to security threats. Each tool serves a unique purpose and has its own strengths and weaknesses. This article provides an overview of these tools, including a practical examples of Yara rules and detailed installation and usage instructions for the Windows enviroment.
Overview
| Tool | Primary Use | Rule Format | Main Strengths |
|---|---|---|---|
| Yara | Malware research and classification | Custom language | Identifying specific file patterns and characteristics |
| Sigma | Log data pattern detection | YAML | Standardized log event detection for SIEM systems |
| Snort | Network intrusion detection | Custom format | Detecting network traffic patterns indicating malicious activity |
Yara rule
Yara is specifically designed for creating and matching patterns in files or data streams. It is primarily used for malware research and classification . Yara rules are written in a custom language that allows researchers to define patterns based on strings , binary sequences , and regular expressions .
Yara rule - Example
Yara Download link :
Create 4 test file with this python script :
1 | # Create test files for Yara rule example |
Create an yara rule file ( rule.yar ) with the content bellow :
I am using
jsonto parse this code block simply because it looks nicer when parsed XDDD
1 | rule ComprehensiveRule { |
Run Yara
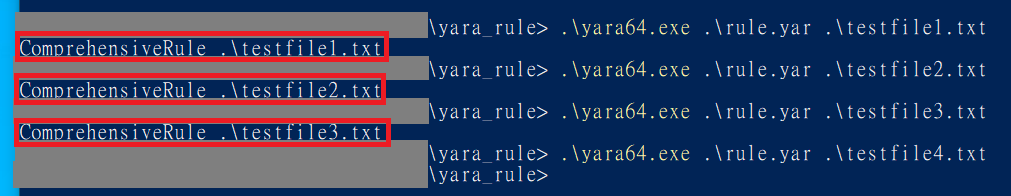
Based on the results, it can be seen that testfile1.txt , testfile2.txt , and testfile3.txt have been detected for their characteristics, while testfile4.txt has not.
Sigma rule
Sigma is a generic signature format used to describe log data patterns in a standardized way. It is primarily used for creating detection rules for security events in log data. The goal of Sigma is to provide a common language for describing log events, which can then be converted to specific queries for various SIEM (Security Information and Event Management) systems.
Key Features of Sigma:
Standardized Format : Sigma uses a YAML format to define rules. This makes the rules easy to read and write, and allows for straightforward conversion to other formats.
Flexibility : Sigma rules can be used with a wide range of log sources, including network devices, operating systems, applications, and security tools.
Compatibility : Sigma rules can be converted into the query languages of different SIEM systems, such as Splunk, ElasticSearch, and ArcSight.
How Sigma Rules Work:
Rule Definition : A Sigma rule is defined in a YAML file, containing several sections such as title, id, description, status, author, logsource, detection, fields, falsepositives, and level.
Detection Logic : The core of a Sigma rule is its detection section, where the conditions for matching log events are defined. These conditions can include strings , regex patterns , and logical operators .
Conversion : Sigma rules are converted to the native query language of the target SIEM system using a converter tool like
sigmac. This ensures that the same Sigma rule can be used across different platforms without manual rewriting.
Example Use Cases:
Detecting Suspicious Command Lines : A Sigma rule can be used to identify suspicious command-line activity, such as the use of PowerShell with certain flags that are often associated with malicious behavior.
Monitoring for Brute Force Attacks : Sigma rules can be set up to detect patterns in authentication logs that indicate brute force attempts, such as repeated failed login attempts followed by a successful login.
Identifying Data Exfiltration : By analyzing log data for large data transfers to external IP addresses, Sigma rules can help detect potential data exfiltration attempts.
Sigma rules themselves do not directly indicate if there is a security threat; they are designed to be translated into SIEM queries that perform the actual detection. Once translated and implemented in a SIEM system like Splunk, the SIEM will execute the query against the collected logs and generate alerts based on the rule's criteria.
For example, after converting the Sigma rule to Splunk format, you can set up a Splunk alert:
Log into Splunk : Access your Splunk instance through a web browser.
Create a New Search : Paste the converted query into the search bar and run it.
Save the Search as an Alert : Click on "Save As" and select "Alert". Configure the alert conditions (e.g., trigger alert if results are found). Set up alert actions (e.g., send email, trigger webhook).
Monitor Alerts : Continuously monitor the alerts generated by the rule and refine the detection logic as needed to reduce false positives and improve accuracy.
Snort rule
Snort is an open-source Intrusion Detection System (IDS) that uses rules to detect and prevent network intrusions and attacks . Snort can be configured to operate as an intrusion detection system (IDS) or an intrusion prevention system (IPS).
Key Features of Snort:
Real-Time Traffic Analysis : Snort performs real-time packet logging and analysis, allowing it to detect a wide range of network attacks and suspicious activities.
Rule-Based Detection : Snort uses a powerful rule-based language to define traffic patterns that should be logged or blocked.
Flexibility and Customization : Users can create custom rules to detect specific threats unique to their environment.
How Snort Rules Work:
Rule Structure : A Snort rule consists of two main parts: the rule header and the rule options. The rule header specifies the action (alert, log, pass), protocol, source and destination IP addresses, and ports. The rule options contain the specific conditions to match, such as content , byte patterns , or regular expressions .
Detection Engine : When Snort analyzes network traffic, it matches packets against the rules in its rule set. If a packet matches a rule, the specified action is taken, such as generating an alert or logging the packet.
Preprocessors : Snort can use preprocessors to analyze and manipulate packets before they are evaluated against the rules. Preprocessors can detect anomalies, normalize packet data, and decode various protocols.
Example Use Cases:
Detecting Malware Traffic : Snort rules can be written to detect network traffic patterns associated with known malware, such as specific HTTP request headers or URI patterns.
Identifying Port Scans : Snort can detect port scanning activity by monitoring for multiple connection attempts to different ports on the same host within a short time frame.
Blocking SQL Injection Attacks : By analyzing HTTP requests for common SQL injection patterns, Snort can identify and block potential SQL injection attempts.
Conclusion
Yara, Sigma, and Snort are powerful tools that serve different purposes in the realm of cybersecurity. Yara excels in identifying specific patterns in files, making it indispensable for malware research and classification . Sigma provides a standardized way to describe log events , enabling consistent and flexible detection across various SIEM systems . Snort offers real-time traffic analysis and intrusion detection , allowing organizations to protect their networks from a wide range of attacks.

